
How Cyber War Games Can Improve Your Cyber Readiness
Technology Solutions
By conducting cyber war games, businesses will feel better prepared in the event of a real-world cyber attack.
After all, without putting your security system to the test, how do you know it will perform?
And, how do you know how your team will react in the case of a real cyber attack?
If this has never happened before, there will be lots of unanswered questions and it could create a great deal of panic. Being prepared is absolutely key, otherwise you’re leaving yourself open to attack.
Cyber wargaming allows you to explore attack & defense scenarios in a simulated and secure environment. By putting your current system to the test, you can identify any vulnerabilities early on, which could be exploited by cyber criminals.
It’s all well and good knowing what your security system is in theory, but seeing how it performs in practice is a whole other matter. It needs to be put under the microscope, and undergo rigorous testing to ensure it is capable of performing.
As a cyber practitioner, your primary responsibility is the safety of the business, related data, and systems. A lot of effort goes into this which can go unnoticed.
If we use the example of a flight attendant, their primary responsibility is ensuring the safety of passengers. However, to ensure this happens, they are constantly undergoing rigorous training of evacuation protocols, distressed passenger scenarios, and first aid training. Knowing how to protect passengers isn’t just a given. They need to re-evaluate their approach, and ensure they understand best practices.
The same goes for a cyber practitioner as you need to be aware of the ever-changing security landscape.
With that said, let’s take a look at cyber war games in more detail and explore the benefits of employing this proactive approach in your own business.
What Are Cyber War Games?
Cyber war games are a way of testing an organisation’s cyber readiness.
Essentially, cyber war games allow you to see how ‘ready’ your current security team and system is in the event of a real-life cyber attack. However, by using planned attack simulations in a secure environment, it’s a safe way of testing your current practices to ensure they are as robust as possible.
These games also allow businesses to practice how to react to different threat scenarios so that they can identify any holes in their processes, readiness, and system. By understanding which gaps currently exist, and how these gaps can be exploited by cyber criminals, you can improve your defense strategy moving forward.
Cyber war games usually involve some of the most common attack methods including DDoS, code injection, reverse engineering, exploitation, evasion techniques, recent vulnerabilities, or brute force attacks.
Wargame strategies relate to common cyber attack pathways such as weak user credentials, malicious insiders, poor encryption, misconfiguration, ransomware, and much more.
By engaging in cyber war games, it helps businesses understand the types of damage that can be caused by cyber attackers. This facilitates better preparation in the event of a crisis by providing greater insight into different cyber risks.
It can also lead to changes in wider organisational policy that speed up mitigation processes and limit the impact of threat.

Who Uses Cyber War Games?
War games are not just conducted in the private sector, but also at state level.
Governments are becoming increasingly concerned about the potentially catastrophic effects of cyber attacks and want to understand how they can mitigate the risks.
Consider how much information these organisations hold. Any sort of cyber attack could be disastrous and personal information could be leaked on a mass scale.
That’s why many countries are engaging in cyber war games to better understand how they can protect important data.
For example, Services Australia hosted a cyber war game event to engage the community and demonstrate the importance of cyber security in the case of a real-life event. As a Government department, they understand the need for skilled staff who can protect organisations, infrastructure and people from cyber criminals.
These war games were conducted by TLR, as we are committed to strengthening people’s knowledge and understanding of current cyber security techniques.
We design, build, and run comprehensive themed Kinetic Cyber Experiences to broaden people’s technical knowledge through fun and relatable exercises.
To find out more about our cyber war games and how these can benefit your business, simply get in touch with the team!
Who Participates in Cyber War Games?
Cyberwar games are modelled from military training exercises, and generally involve a red team, a blue team, and a white team.
All of these teams play a very important role, and the simulation exercise allows an organisation to test its defense strategy.
Let’s take a look at these teams in more detail, and identify why they are important for your cybersecurity system.
A Red Team
The red team represents the attackers. Generally, this team is made up of offensive security experts who try to attack the organisations’ network using sophisticated techniques.
They initially obtain access by stealing user credentials or through social engineering methods. Once inside the network, they move swiftly through the system, trying to get as deep as possible without being detected.
This allows them to progress even further whilst also exfiltrating data.
Including team members who are traditionally defense focused to the red team has significant advantages. Allowing defenders to work from the opposite vantage point provides an opportunity to better understand the psyche of attackers. Knowing how attackers work is one of the best ways for a defender to be more prepared.
What is red teaming and why does your business need it?
Red teaming plays a vital role in accurately assessing your organisations prevention, detection, and remediation capabilities.
By systematically and rigorously identifying a path of attack that breaches an organisations defense system, it allows individuals to see how their security tools would actually perform. It’s not a theoretical approach, but instead, a practical approach as existing security systems are put to the test in a simulated environment.
This practical approach clearly articulates weaknesses in the defenses and can help demonstrate to upper management the need for additional defensive measures.
Red teaming exercises
Red teams use a range of techniques to exploit gaps within a security network and to find vulnerabilities.
Red team activities commonly follow the MITRE ATT&CK Framework, which is a globally-accessible knowledge base of tactics and techniques based on real-world experiences and events.
The framework can be used to help organisations develop a robust prevention, detection, and response system that can be customised to their individual needs.
Examples of red teaming exercises are as follows:
- Penetration testing which involves a red team member trying to gain access to the system using a variety of real-world tactics and techniques.
- Social engineering methods which aim to manipulate employees or other network members so that they share or disclose important information.
- Intercepting communication to gain more information about the security network in order to evade existing security techniques.
- Cloning an administrator’s access cards to gain entry into unrestricted areas.
- Performing DNS research
- Conducting digital analysis to create a baseline of network activity and more easily spot unusual or suspicious activity
- Reviewing, configuring and monitoring security software throughout the environment
- Ensuring perimeter security methods, such as firewalls, antivirus and anti-malware software, are properly configured and up-to-date
- Employing least-privilege access, which means that the organisation grants the lowest level of access possible to each user or device to help limit lateral movement across the network in the event of a breach
- Leveraging microsegmentation, a security technique that involves dividing perimeters into small zones to maintain separate access to every part of the network

A Blue Team
The blue team represents the defenders and responds to attacks inflicted by the red team. Think of it this way, if the red team is playing offense, then the blue team is playing defense.
It’s the perfect combination to ensure your security system is robust and protected against cyber criminals.
Generally, this team is made up of incident response consultants who are responsible for advising the IT security team on where to make improvements to prevent cyber attacks. It is then the job of the IT team to maintain the internal network against various types of cyber risks.
What is blue teaming and why does your business need it?
Whilst many organisations consider prevention the most important aspect of cyber security, this is incorrect. Detection and remediation are equally as important as you can’t wait for a cyber attack to happen – you need to be prepared.
That’s why blue teaming exercises are key, as they allow you to actively test your existing cyber defenses and capabilities in a low-risk environment.
This is something we’re very passionate about at TLR, as we want to make you cyber resilient. We don’t just want you to be reactive, we want you to be proactive so that you are in the best possible position to protect your data should a cyber attack occur.
Blue teaming exercises
The blue team exists to defend the organisations security system by using tools, protocols, systems, and other resources to protect the existing infrastructure.
These exercises are designed to identify gaps in the capabilities of a security system so that the strategy can be improved going forward.
It’s critical that the blue team’s environment emulates the organisation’s current security system, which may have misconfigured tools, unpatched software or other unknown risks. This makes the exercise more effective as it is an accurate representation of the real setting.
Examples of blue teaming exercises are as follows:
A White Team
This team is neutral and is responsible for the infrastructure. They are also responsible for referring to any engagement between the red team and the blue team.
Participants in cyber war games generally involve security specialists, systems engineers, information security managers, regulatory experts, and developers with technical knowledge.
On top of this, participants should also include legal and public relations teams as these individuals are responsible for managing the public response during a real-life cyber attack.
Ultimately, the aim is to help organisations identify their key weaknesses, so that they can improve their defense system.
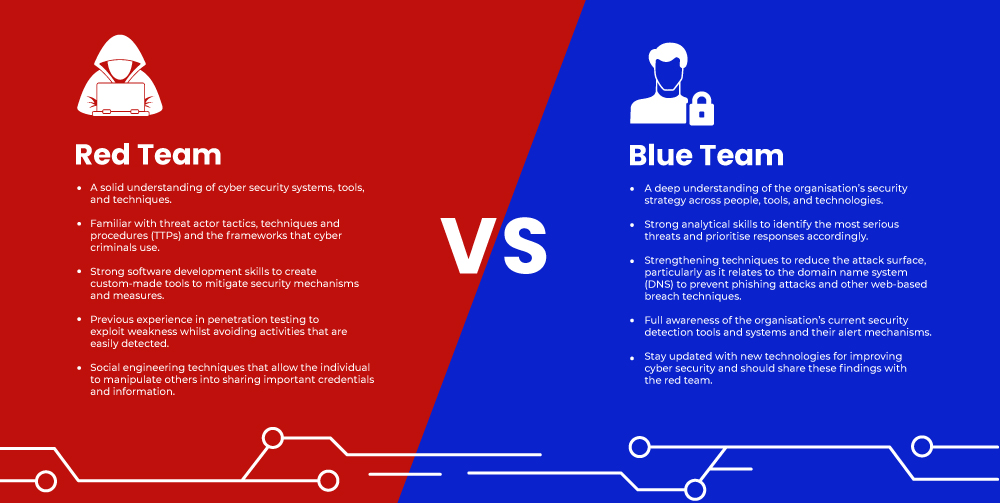
Red Team vs Blue Team Skill Set
To be successful on the red team, you must be devious in nature and adopt the mindset of a sophisticated adversary. This allows you to gain access to a security network to steal important information without being detected.
In contrast, a member of the blue team must be heavily focused on defense and be proactive in nature. They need to identify potential problems before they have a chance to inflict damage on a security system.
To explain these differences in full, take a look at the below infographic:
At TLR, we want to take the pressure off your existing security team. We know that they already have their hands full and have other tasks to concentrate on.
Want to give time back to your IT team without compromising your defense strategy?
Cavalry is an automated solution which constantly analyses and detects security or vulnerability issues within your organisation’s network. It’s more than just a vulnerability scanner, as the Cavalry enhances human operators.
This allows your IT team to get back to other jobs, safe in the knowledge that your cybersecurity is taken care of.
To find out more about this solution, get in touch with a member of our team.
Key Benefits of Cyber War Games
There are various benefits of running cyber war games, most notably because it brings different teams together. These games enable individuals to collaborate in a simulated attack to sharpen their capabilities and to work out how to respond.
Below, are some of the types of knowledge, skills, and experiences that wargaming can provide:
Handling a variety of situations
Cyber war games prepare your team for a wide variety of situations. Whether that’s preventing a cyber attack from happening in the first place, to stopping a cyber attack in its initial stages once a network has been penetrated, it makes your team much more agile.
Better decision-making capabilities
Decisions need to be made very quickly, otherwise you’re giving hackers more time to penetrate your network. In cyber war games, everything happens under intense pressure which better prepares individuals for a real-life cyber attack.
It gives your team an idea of what they can expect, and the timeframe that they need to respond. When your organisation is under attack, it’s absolutely essential that these decisions are quick, clear, and understandable otherwise lots of sensitive information could be leaked.
In fact, in some state-sponsored attack simulations, the stakes are even higher with human safety at risk.

Expands your knowledge base
By simulating a real-world cyber attack, it helps team members expand their knowledge and improve their current skill set as they will be tackling possible threats. As such, this broadens their experience and allows individuals to contribute more actively to the development of cyber attack defenses.
Enables groups to collaborate
In cyber war games, teams will need to work together to identify solutions under pressure. As such, this helps prepare them for a real-world attack as they will need to think and act quickly.
Cyber war games also bring people together who may have varying knowledge levels and different organisational cultures. Therefore, they will have to combine these skills and work out the correct response.
Improving current policies
Cyber wargaming improves your teams knowledge of different regulations and helps them be better prepared for inspection and review processes. This provides the perfect opportunity for them to revisit their own cyber security defense system to make sure it is as robust as possible.
By determining areas of improvement in defensive incident response processes, they can build a more robust defense moving forward.

How Cyber War Games Can Improve Your Cyber Readiness
Cyber war games help make you more cyber resilient.
Cyber threats are becoming increasingly sophisticated and frequent, across both private and government sectors.
To prepare for this event, organisations must evaluate their existing cyber security tools to understand where threats are coming from so that they know how to respond.
Waiting for this to happen isn’t an option. You can’t sit back and be complacent, assuming that your current security system is up to the job.
You need to be ready to respond to a cyber attack, and being able to do this in a simulated environment allows you to test your response, identify capability gaps, and advance your readiness techniques.
At TLR, we help numerous companies become more cyber offensive. We eliminate the stigma of fear that surrounds cyber security, and empower your team to deal with any situation that may arise. For more information about how we can help, get in touch with our team of experts.


