CAVS
A continuous automated attack surface management and mapping solution that analyses and detects security misconfigurations and vulnerabilities within your organisation's network.
CAVS provides a bundled technology solution aimed at bolstering network security by automating vulnerability detection while enhancing the effectiveness of human operators.
Engineered by TLR’s leading Penetration Testers and Software Developers, CAVS leverages advanced tools and techniques derived from manual penetration testing (pentests). This ensures rapid identification of vulnerabilities, exceeding the effectiveness of conventional manual approaches.
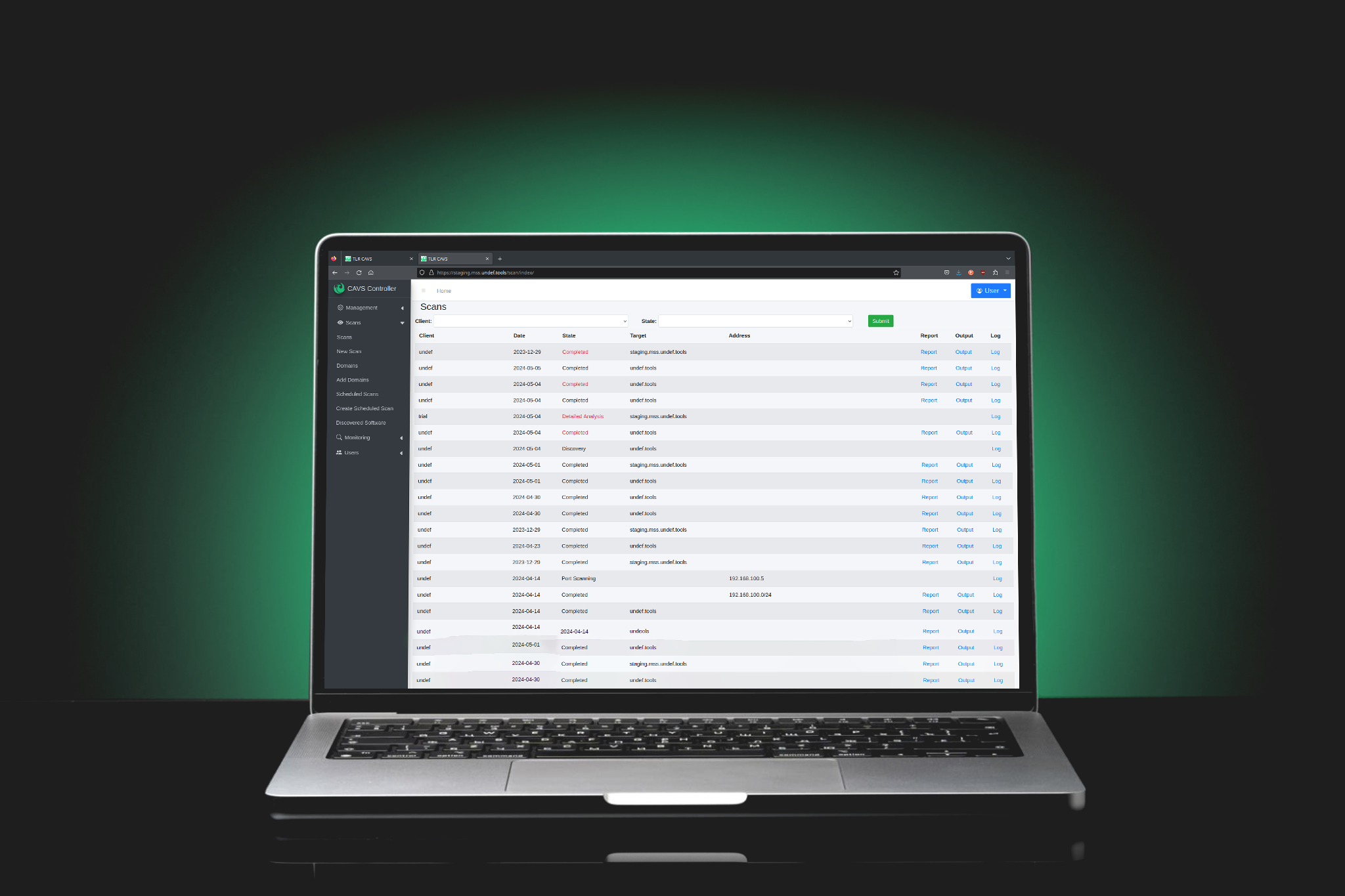
Each scan initiates automated system discovery, alleviating the need for manual environmental knowledge. CAVS effectively identifies all assets, even those overlooked by your team. Giving you visibility of your attack surface.
The system regularly scans your infrastructure, swiftly uncovering potential security threats with portal access to manage your organisation and initiate scans on-demand or schedule them in advance.
Executive summary reports tailored for management, as well as detailed reports that highlight vulnerability issues, complete with prioritisation and recommendations.
Also referred to as Attack Surface Management, is a core function of CAVS, ensuring comprehensive identification of all assets associated with your organisation.
CAVS offers significantly greater cost-effectiveness compared to traditional manual penetration tests, maximising the insights derived from your security budget.
Automated regular scans provide assurance that your infrastructure undergoes consistent and methodical review, ensuring accuracy in the assessment process.
CAVS streamlines pentesting and scanning tasks, freeing up security teams to focus on addressing critical security challenges.
All scans automatically run in the background, ensuring uninterrupted network coverage and allowing your business operations to continue without disruption.
CAVS optimises operations, through automated scanning and reporting, conserving time and resources while maintaining rigorous security standards. By minimising the manual workload associated with vulnerability detection and reporting, CAVS empowers human operators to focus on higher-level tasks.
CAVS constantly analyses and detects security or vulnerability issues within your organisation's external and internal networks.
CAVS proactively identifies and alerts users to potential security threats, allowing you to take pre-emptive action before breaches occur.
CAVS delivers comprehensive reports on-demand, providing actionable insights into your network's security posture.
Choose between remotely hosted or on-premises deployment to suit your specific requirements and preferences.
Scanners can easily be scaled up or down depending on your network size or deadlines.
CAVS finds systems you did not know existed.
Discovers undesirable public access to management ports.
Alerts when it can log in using publicly available defaults.
These are generated at Manager, SOC Operator and SIEM levels to best fit your organisation.
Works against IPv6 only cloud services.
Uses common pen-testing tools to discover vulnerabilities in web applications automatically.
Reports on both the validity of TLS certificates as well as the security of specific settings use.
CAVS assesses the content security policy of your websites for potential holes.
CAVS reports all CVEs that match your deployed software with links to vendor patches.
CAVS can be configured to report only on changes to your systems, alerting you to unexpected new systems and new potential security holes.
Optionally self host and retain complete control of your vulnerability data, or use our cloud service for single-click delivery.
The scans start with a discovery phase to identify all assets within scope, even ones you may not know about. The scan can run and be altered as often as desired depending on network size and complexity.
The CAVS platform then automatically gathers information about the target network and identifies new systems and potential weaknesses through known vulnerabilities and identification of configuration issues in systems.
Detailed scan reports are then generated. Any vulnerabilities are then analysed and remediation work packages are produced, providing advice to correct the issue if possible. CAVS results can also be delivered programmatically to other security tools like a SIEM.
Up to 15 Hosts |
Up to 40 Hosts |
40+ Hosts |
||||
|---|---|---|---|---|---|---|
Managed |
Managed Premium |
Managed |
Managed Premium |
Managed |
Managed Premium |
|
| Continuous Automated Vulnerability Scanning | ||||||
| Target Network Discovery (Future Map) | ||||||
| CAVS Cloud Access | ||||||
| Target Blacklisting/Exclusions | ||||||
| User Management (Future RBAC) | ||||||
| Summary Reports | ||||||
| Detailed Reports | ||||||
| Custom Scan Schedules | ||||||
| Email Support/Service Desk | ||||||
| Online CAVS Portal Training Documentation | ||||||
| CAVS Portal Training via Remote Meeting (Teams/Zoom) | ||||||
| SOC/SIEM/DevSecOps Ingestible Reports | ||||||
| Executive Reports | ||||||
| Report Consultation | ||||||
| Priority Support | ||||||
| Remediation Scripts Library Access | ||||||
| Out of Schedule Validation Scan & Report (3 per annum) | ||||||
| Cloud Based or On-Premise Dedicated Management Server | ||||||
| Client Internal Scanner Deployment | ||||||
| Remote Remediation |
With CAVS we can point out what you don’t know about your environment. A scan from CAVS will quickly uncover tactical security exposures. Perhaps more importantly, they inform strategic, evidence-based security decision making.
We have designed our scans to take approximately one week. The time can run longer for large and complex environments. We know you’re busy, and if you need information more quickly, there are a lot of dials we can turn to meet your deadlines.
A target is any single digital asset detected by the CAVS discovery system. If you’re doing an external scan that will include internet-facing IP addresses, hostnames, web servers, mail servers, management interfaces, etc.
Internal scans are focused on the infrastructure behind your firewall. This requires that we install scanners within your network. It can be on your hardware, a virtual machine (VM) or hardware we provision. External scans target internet-facing systems like web servers. This shows you exactly how you look from the attacker’s perspective.





“The Cyber War Games Challenge System has engaged the students and Cyber stakeholders, making it a focal point of TasTAFE’s training SOC. The Lego build is attractive and has strengthened links with local industry and other educational providers. It is an excellent product, technically appropriate for cyber security training, visually engaging and the production and support team have been excellent, timely and very enthusiastic.”