
What Is a Data Leak and How Is it Different to a Data Breach?
All
When considering how best to protect your network internally, you may find yourself asking ‘what is a data leak?’
It’s important to know the difference between a data leak and a data breach as data leaks often happen internally and can be unintentionally carried out by one of your employees.
Therefore, a data leak is not so much an attack, but more of an internal error.
This error can however lead to a further cyber attack, so it’s still important to mitigate data leaks wherever possible to ensure the safety of the data within your organisation.
In this post we will highlight the distinction between a data leak and a data breach, outline how data leaks occur and provide some measures your company can take to prevent the leaking of confidential information.
So, let’s get started
What Is a Data Leak?
A data leak occurs when sensitive data is accidentally exposed either on the internet or another form such as lost hard drives or devices.
Data leaks usually occur through an internal source leaking company data often accidentally or unintentionally.
However, cyber criminals can orchestrate a data leak by performing another type of cyber attack first such as a password attack, stealing credentials, and going on to leak data from accounts.
However, cyber criminals don’t have to conduct an attack to gain access to data as with a data leak the information is already there for them to take.
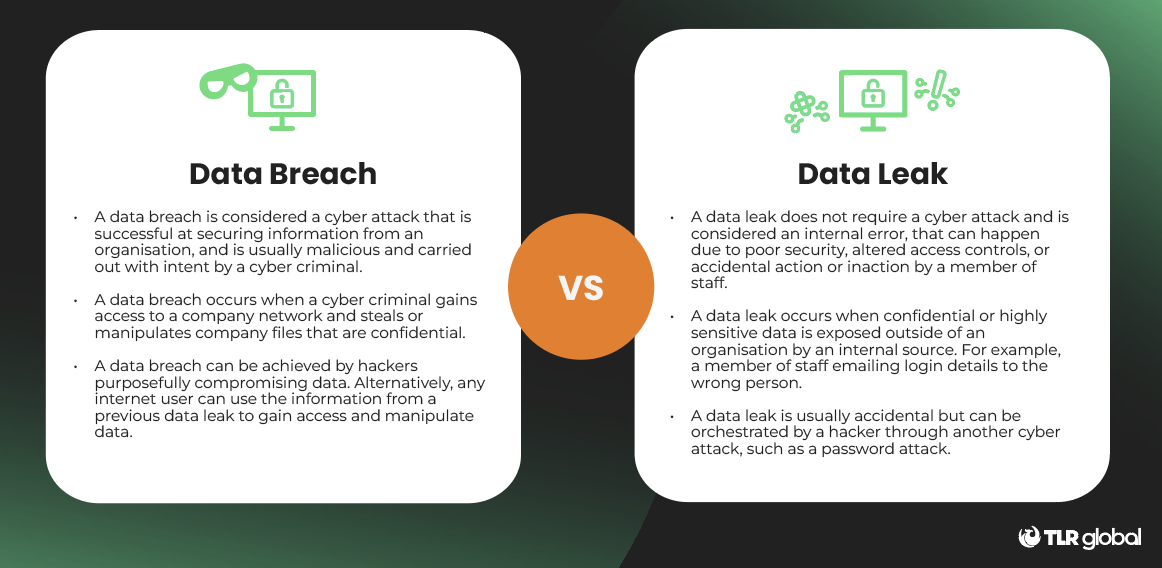
What Is the Difference Between a Data Leak and a Data Breach?
The two terms data leak and data breach are often used interchangeably and mixed up, however there is a distinct difference between the two.
While both a leak and a breach involve the unauthorised exposure of data, it’s the cause of exposure that’s different, so let’s break it down.
A data breach is a cyber attack that is successful in securing sensitive information from an organisation.
A data leak on the other hand does not require a cyber attack and can happen due to poor security, or an accidental action or inaction by an individual within the company.
The simplest way to differentiate the two attacks is to remember that a leak is usually accidental and a breach is usually intentional and malicious.
In some circumstances, one attack can lead to another, as an attacker may use the information they steal from a leak to launch their own data breach attack.
Criminals only need one data leak to turn it into a wide-scale data breach, and this makes leaks just as much of a threat as a breach.
How Do Data Leaks Happen?
There are a variety of methods hackers can use to get into a network and steal data, however data leaks are slightly different.
As this type of data issue occurs due to an internal error or inaction, data leaks act as more of a stepping stone for a further cyber attack.
So, usually data leaks occur first and provide a platform for cyber threat actors to go on to conduct other attacks involving phishing, ransomware, or other harmful viruses.
There are some causes that are more common than others so let’s take a look at how they occur.
Poor Security Architecture
Often if your cyber security architecture is misconfigured or unpatched, this can lead to data being exposed unintentionally.
This may occur due to the wrong settings or access permissions that havent been updated, or even software that is outdated. Whilst all of these may seem harmless, they can lead to data being exposed.
Poor Credential Policies
It’s a general trend across the world that people often use the same passwords for a range of accounts across their working and personal lives.
These passwords are often copied and poorly constructed using names, dates, numbers, or phrases that may be easier to remember for users, but are equally easy for hackers to guess.
This is considered a password attack and it comes in a variety of forms, from using software to test billions of combinations, to phishing emails.
Therefore choosing poor credentials can contribute towards a data leak as hackers can use a password attack to obtain passwords and login details, access accounts, and leak the information they find.
Equally, choosing poor credentials can result in the exposure of several accounts at once, as something as simple as writing passwords in a notebook on your desk could lead to a data leak.

Social Engineering Attacks
Although data leaks are usually accidental so can’t always be considered a malicious cyber attack, criminals can create data leaks using the same method as a data breach.
For example, a phishing email may successfully gain access to a user’s login details, which then allows a hacker to conduct a data breach on a larger scale.
On the other hand it may be that your credentials have been used in a data leak already and are made available on disreputable websites leading to hackers conducting credential stuffing. This means hackers can steal these details as well as information.
This is considered a social engineering attack as hackers use the data leak in order to launch another form of cyber attack.
Lost Devices
Whether your employees use company devices such as laptops, tablets or mobile phones, inside or outside of work, there is always the potential for devices to be lost.
As this is unintentional on the part of the employee, this would class as a data leak.
If this happens then it will likely result in lost company information too as files and documents will be saved onto employees’ devices or this information may have been recently accessed and easy to find.
For example, if a hacker gains access to the device they can check the computer history or password auto-fill settings and gain access to a variety of accounts and quite possibly confidential company information.
If an attacker then acquires access to the device and the content stored on it, this could further lead to identity theft or a subsequent data breach.

How to Prevent Data Leaks
Data leaks are mostly caused by operational issues within a business, often due to technical or human errors.
In order to prevent leaks from occurring, it’s important to start with a multi-layered cyber security approach including a robust security system provided by your IT security team.
However, although this system should detect and prevent the majority of cyber security attacks, it’s impossible to be prepared for every single attack as new methods are always emerging.
Therefore, it’s important to have an incident response policy in place to help with the recovery process if a cyber attacker is successful and the measures you have in place don’t quite work or aren’t implemented in time.
But first it’s important to put policies in place to prevent attacks, so let’s look at a few procedures your organisation can adopt to prevent a data leak turning into a data breach.
Assess and Audit Security
One way to detect gaps in your security architecture is to hire an external third party to conduct a cyber security audit.
This is necessary to ensure you are fully compliant with the statutory standards and regulations set by national and international institutions, such as the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO).
Cyber security audits help to verify that your business has the right safeguards and policies in place to protect confidential and private company data and to prevent attacks as much as possible.
Once an audit has been conducted, your IT security team will be able to plug the gaps in your network that have been missed and provide insight into what the company must do next to prevent data leaks or any other cyber attacks.
Data Access Restrictions
One action companies can take without the need for a third party or even the in-house cyber security team is change the access settings for company files.
This is particularly important for confidential files that contain sensitive, financial or legal information, however access should be regularly monitored throughout the entire company across all files.
Depending on the level employees are working at, access restrictions should and will be different particularly for the documents and files that are more sensitive.
These access controls should be reviewed regularly to ensure that employees have the right levels of access, for example a senior level employee is likely to have a higher level of access due to their position.
However, a new starter or employee working in an entry-level position will probably only need a limited amount of access to certain files depending on their job role.
This should be monitored as although it may be unintentional, data leaks can still occur if the wrong level of access is given to the wrong employee.
Off-Boarding Employees
Linking on from access restrictions, off-boarding employees is a process that should also be conducted properly, as this could be the difference between safe data and a data leak.
Off-boarding employees involves removing all access for those who are leaving your company.
This should be done accurately and involves removing access to all files, software systems, and deleting accounts, to ensure there is no way for employees to regain access to the company network or anything stored within.
Equally, this includes company equipment as if employees hold onto devices such as laptops
and mobile phones, data may be stored on the device that they should no longer have access to and this could easily lead to a data leak.

Provide Cyber Security Awareness Training for Employees
All employees should receive adequate training on cyber security awareness as your team are essentially another line of defence if the measures you have in place fail to prevent attacks.
In your organisation you should provide training on how to spot the signs of a potential attack, particularly common attacks such as phishing emails, password attacks, data leaks, and data breaches.
These are the most important areas to begin with for businesses as these attacks often occur day-to-day and it’s often best practice to ensure your entire organisation is clued up on spotting the basics first.
At TLR we provide a variety of training options from cyber war games, to training bootcamps offering various levels of education on cyber security awareness.
Our cyber war games allow teams of your employees to be entered into a simulated cyber attack situation and provide them with the tools and knowledge to be able to stop the attack and save the company.
On the other hand, our training boot camps consist of baseline training and as well as a second level course, helping to expand the cyber security knowledge within your team.
Implement Multi-Factor Authentication
Although strong credentials will help to prevent data leaks to a certain extent, multi-factor authentication (MFA) adds another layer of protection to accounts across the company.
Using MFA across your organisation will help to boost the effectiveness of the passwords you use as it’s not always enough to rely on passwords alone to prevent attacks from occurring.
As we have previously mentioned, there are a variety of password attacks that can often render your password protection policies useless and this is where MFA comes in as it ensures a password leak isn’t enough to cause any further harm.
For multi-factor authentication to work, employees must register their phone or another account to receive a one time passcode, or use their fingerprint as another form of identification.
This helps to protect company accounts as it is unlikely hackers will have access to numerous accounts of fingerprint identification, and creates a wall between cyber criminals and private company data.
What Is a Data Leak and How Is it Different to a Data Breach?
Although not necessarily regarded as a cyber attack, data leaks can create the perfect platform for hackers to gain access to information and perform more malicious data breaches.
Therefore, it’s important to combat data leaks internally by training staff, creating and updating password and MFA policies, and hiring an auditor to check your architecture is strong and secure.
By doing so you can limit the amount of data leaks happening internally which in turn decreases the amount of hackers who can use leaked information against you and your organisation.
At TLR our experts can help to prepare your organisation for data leaks of any kind, whether they’re internal or external to ensure cyber criminals don’t take advantage and launch a full cyber attack.
If your organisation could benefit from some of TLRs training programmes or technological solutions to help resolve gaps in your cyber security architecture, get in touch today!


