SETH
An automated solution that identifies vulnerabilities and breaches in your network and infrastructure and automatically resolves them.
While Security Operations Centres (SOCs) are common, our SETH system takes it further. It automatically detects suspicious behaviour and deploys microbots to address issues, freeing SOC operators for critical tasks.
Similarly, our SETH system enhances security orchestration. It detects and addresses network issues autonomously, allowing SOC operators to focus on essential tasks.
With TLR’s advanced solutions, organizations can efficiently manage security threats and optimise SOC operations.
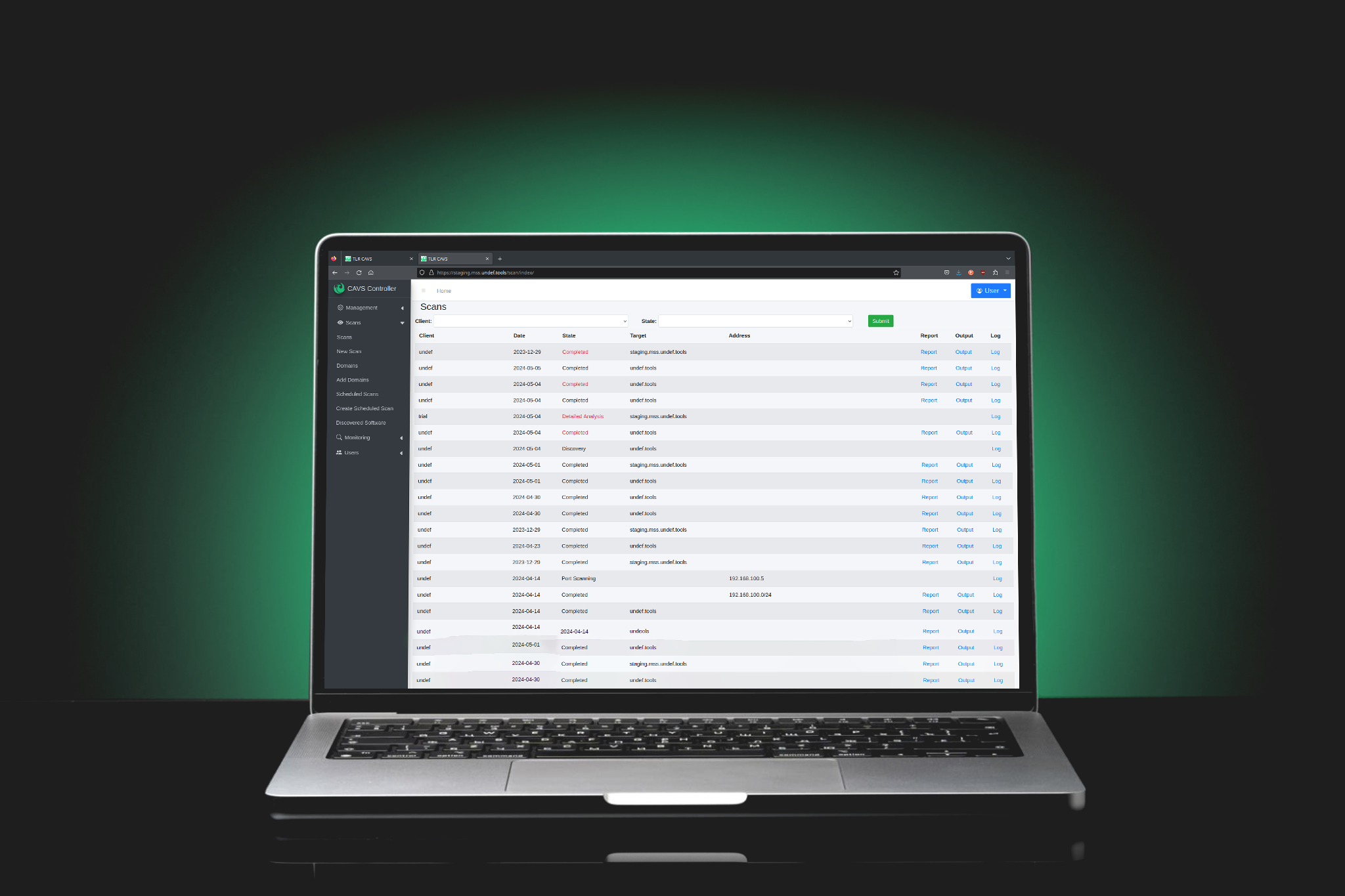
Maximises your IT department's time by freeing them from tedious manual tasks, allowing them to focus on the bigger picture.
Automatically finds and rectifies issues before they become critical.
Finds and resolves suspicious behaviour with your network efficiently and effectively.
The SETH is highly customisable. Start with one or two modules to get instant return on investment. Add new modules as your security needs evolve.
The Active Directory module comes standard, so you get out-of-the-box account takeover defence.
The SETH modules help to defend against ransomware by blocking malicious processes, protecting crown jewels, and restricting system access.
Whether your organisation is pursuing the top four, the essential eight, SOC 2, NIST, CMMC or any of the many compliance standards, SETH can support these efforts and get you on your way to compliance certification.
Combine Local Account Management module, Application Whitelisting, & Scheduled Task Monitoring for a robust Endpoint Security package.
Making sense of threat intel is time-consuming; making threat intel actionable takes even more time. SETH with digital risk protection services can consume threat intelligence and remediate threats without any need for intervention.
Maximise uptime by automatically finding and fixing issues that could eat up valuable IT time.
Attackers and malware attempt to create new administrator accounts or modify existing accounts and groups to take over your network. ADM ensures Active Directory integrity with: Privileged Group Management & Monitoring Domain User Monitoring Group Policy Monitoring
Once in your environment, attackers target critical & sensitive files. They can be exfiltrated, deleted or, in the case of ransomware attacks, encrypted. The File Monitoring module has a proprietary method for protecting these critical files and maintaining file integrity.
Malware and other malicious activities often create new processes designed to steal data or facilitate other cyber-attacks. Process Tracking & Learning combats this by: Tracking and learning about legitimate processes in the system Alerting on unexpected processes Optionally allowing administrators to block new processes automatically
Similarly, when attackers attempt to make an account in Active Directory, malware often creates an administrator or root account with escalated permissions. This module monitors servers or endpoints for creating new accounts or unauthorised attempts at modifying existing accounts.
Malware will often attack critical applications such as anti-virus. Working on its own or in conjunction with existing whitelisting capabilities, this module can act as another layer of defence against attackers trying to terminate critical processes.
Attackers use scheduled tasks to create persistence and control systems. This module will monitor for unauthorised tasks and take remediation action if the organisation desires.
Unpatched systems connected to the network introduce threats to critical assets. If your systems aren’t up to date, then you are more likely to be compromised by the latest vulnerabilities. Windows Patch Monitoring will alert your SOC team when Windows patches haven’t been installed so your team can act quickly with focus and intent.
It is laborious to manually process Threat Intelligence and Indicators of Compromise (IOCs). Most organisations don’t get good value from these services. The ATIM module ingests threat intelligence and IOCs, then hunts within your network and identifies critical assets that may be affected by these indicators.
Attackers will attempt to exploit known vulnerabilities on servers with malicious commands. This module detects these malicious commands and helps prevent the exploitation from occurring. The Log4j fallout inspired the development of this module, and it has been adapted to support ANY hunt exercise.
Monitor critical assets within your network. Collecting behavioural data which reports back to central management systems and correlates against our Threat Intelligence.
SETH automatically deploys our “hunting” bots, finding suspicious network behaviour and controlling it, shutting it down and reporting relevant data to the SOC.
Reducing the need for human intervention, SETH frees up SOC managers to do more valuable and critical tasks. Failures and outages are then automatically resolved or reported back to SOC managers alerting them to the issue.
No, you absolutely do not. We don’t actually recommend you start with all of them. While many modules are complementary, they can operate independently. We first consider what your business needs are and align these with the security efforts provided by SETH.
Both Windows and Linux are largely supported. In some situations, like the Active Directory module or Windows Patch Monitoring, only Windows is supported.





“The Cyber War Games Challenge System has engaged the students and Cyber stakeholders, making it a focal point of TasTAFE’s training SOC. The Lego build is attractive and has strengthened links with local industry and other educational providers. It is an excellent product, technically appropriate for cyber security training, visually engaging and the production and support team have been excellent, timely and very enthusiastic.”